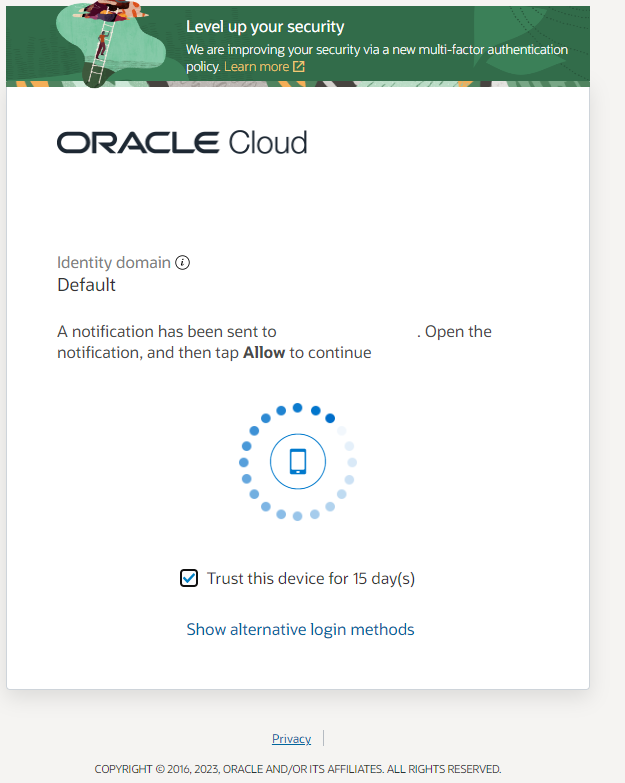
When signing up, it is mandatory to configure and enable Multi-Factor Authentication (MFA). Once configured, during the login process, you will be required to obtain approval either through the Oracle Authenticator App or by obtaining a passcode.
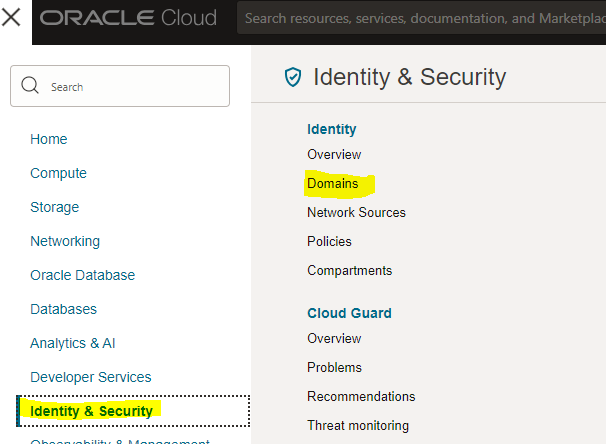
To customise the MFA Configuration, access the Identity & Security section and select the desired domain. This action will direct you to the Domain Dashboard, where you can choose the appropriate security settings and explore additional options for Multi-Factor Authentication.
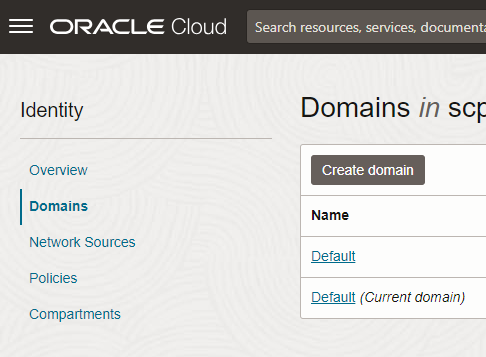
You can change the Default Configuration under Identity–>Domains–>Default domain–>Security –>MFA, when you try to update the changes , you may get the error as below “You cannot disable these factors as they are being referenced in Rules used in Sign-On Policies. Remove them from the Rules before disabling the factors.”
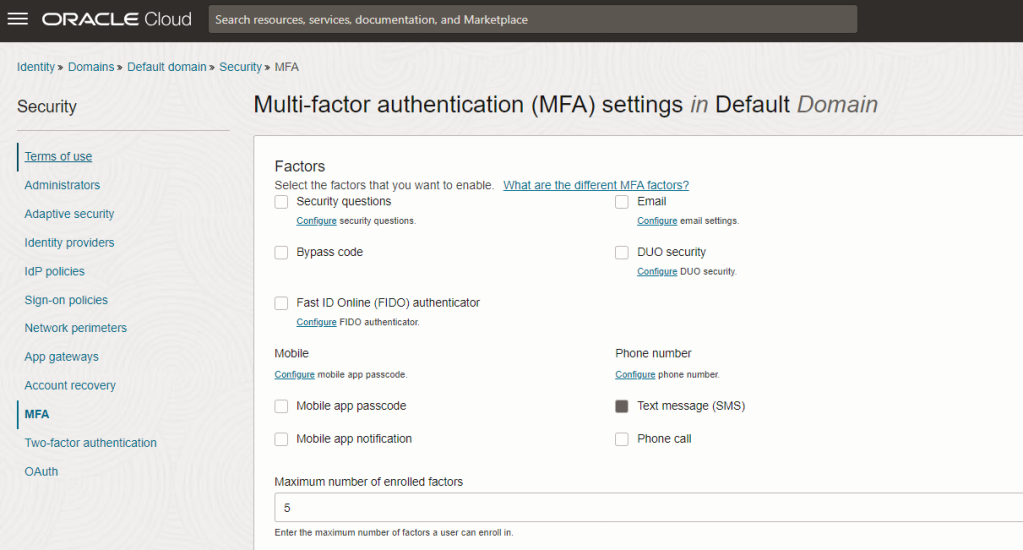
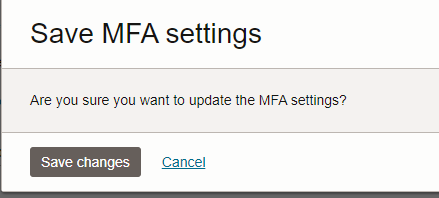
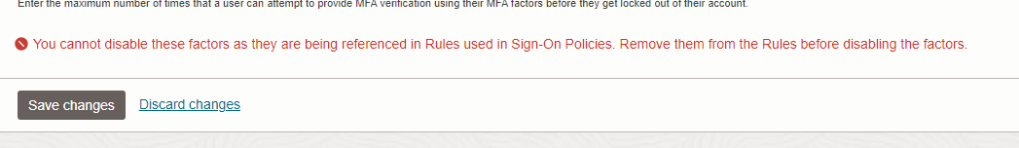
In order to prevent the occurrence of the aforementioned error, it is advisable to disable the default sign-in policy for both users and administrators as indicated in the error message.
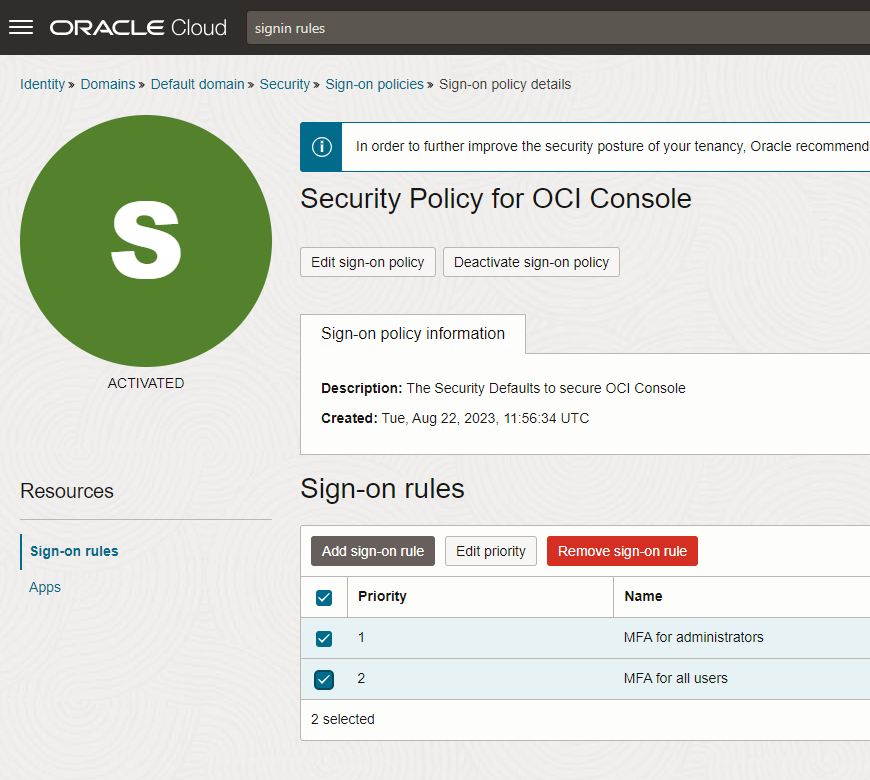
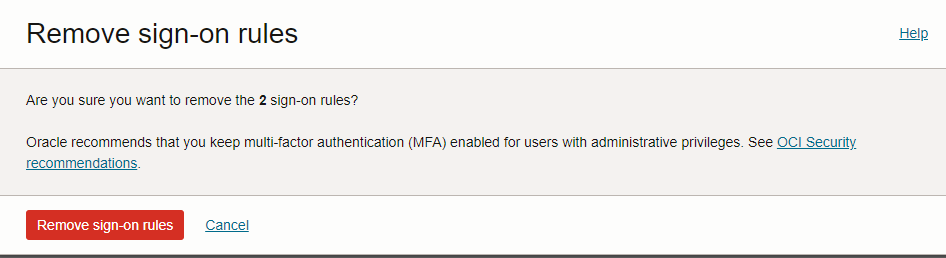
Please note that it is not advisable to disable security policies and multi-factor authentication (MFA) for cloud access. follow https://docs.oracle.com/en-us/iaas/Content/Security/Reference/iam_security_topic-IAM_MFA.htm for more information.
Reference












